The Pane Applications
Uninstallation Assistant
Applications that strictly comply with Apple’s software design guidelines for macOS and don’t need to be deeply integrated into the operating system, are usually installed by a simple “drag and drop” operation. This means no actual installation is necessary, you just drag the application icon into one of your application folders and can launch it immediately.
However, macOS automatically creates additional files when you work with a new application, for example files to store the personal settings for each user, or cache folders for download files, when applications are accessing the Internet to search for automatic updates, etc. You can simply “uninstall” a drag-and-drop application by dragging its icon to the Trash. This won’t remove all the aforementioned other support files, however. This is where the uninstallation assistant of TinkerTool System can help.
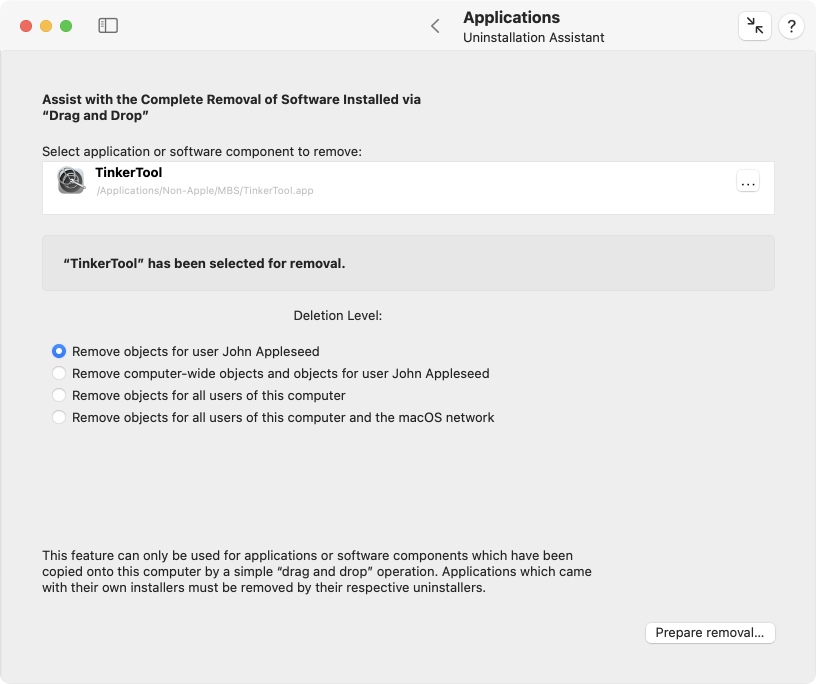
Removing software components and associated files
The job of the uninstallation assistant is to help you to identify all associated components that might have been created by the software component you want to remove. You can let TinkerTool System automatically remove the other files and folders as well, cleaning the entire computer. There are in fact four different levels of clean-up you can choose from:
- You can restrict the search to components which have been created for your user account only.
- You can search for components that have been installed for “computer-wide” usage by all users of the local computer and the personal items of your user account.
- You can search for components which have been installed as personal items for all user accounts known to the local computer, including components which have been installed for computer-wide usage.
- You can additionally include items which have been installed for “network-wide” usage. This is useful if you are using a central software distribution server and the management features of macOS which store information in the /Network/Applications and /Network/Library folders.
If you are using the search levels (3) or (4), TinkerTool System will allow you to delete files and folders which are owned by other users. This is a dangerous option which should be used by experienced system administrators only. Please verify each object carefully before you are actually going to delete it.
There are applications which completely hide where and how they store the data or documents you create when using that application (“shoebox apps”). Other applications may give you a choice to define individual file names for documents, but also use their own private area to store the files. Please keep in mind that the user documents created by such applications might be removed as well when you perform an uninstallation.
Before any object is removed, TinkerTool System will list each affected item. You can then decide for each single object whether you actually want to remove it. Perform the following steps:
- Open the sub-item Uninstallation Assistant on the pane Applications.
- Drag the icon of the program you like to remove from the Finder into the field Select application or software component to remove. You can also click the button […] to navigate to the object, or click on the white area to enter the UNIX path of the object.
- If an application was selected, you have to choose between one of the four possible search levels discussed above, using the buttons at Deletion Level. This step is not necessary if you have selected a component which is not an application.
- Click the button Prepare removal….
Note that nothing is going to be removed yet. TinkerTool System will always analyze your selection first and display the items which would be affected. The program will begin to search for these objects after you have clicked the Prepare removal… button. You can interrupt and cancel the search at any time by clicking the Stop button which will appear while the search is running. Note that a search run can take several minutes if your computer or your network hosts a high number of user accounts and you have selected one of the search levels affecting each user.
After the search has ended, all candidates for possible removal will be listed in a table. The table contains the following columns:
- Remove: Set or deactivate the check mark to include or exclude the affected object from removal.
- Object: Icon, name and path of the object which is suggested for removal.
- Type: the role this object plays in respect to the software component you want to remove.
- Owner: the short name of the user who owns this object. Be very careful if you are going to delete personal items of other users.
- Size: the storage size of the object. This space will be freed when the object is going to be deleted.
- Last change: date and time when the object was modified last.
- Show: click the button in the Show column to display this object in the Finder.
The total number of selected objects and the total storage size is displayed right under the table. The two buttons in the lower left corner allow you to select
- if you want to put the items marked for removal into your Trash, or
- if you want to delete the marked items immediately.
TinkerTool System does not allow you to bypass the security features of macOS. Although this feature allows you to delete objects owned by other users, you cannot use it to spy out the contents of private files. For this reason, it is not possible to display detail information of files which are neither owned by you or by the operating system, or to move items to the Trash for which you don’t have access.
The selected objects will be removed when you click the Remove button. All objects remain untouched when clicking the Cancel button.
TinkerTool System automatically creates a detailed report on the components you are removing. It will be displayed after and while the removal takes place. After the operation has been completed, you can either save the report to a text file, or print it by clicking the respective buttons in the report sheet.
The list of objects suggested for removal is computed according to Apple’s software design guidelines for macOS. Please note that a few applications may not be fully compliant with these guidelines. In this case, the list of removal candidates might not be complete. This means there could be objects which have been created by the application in question, but have been omitted in the list. It could also occur (although this is very unlikely) that objects are included in the list but have actually not been created by the selected application, so they should not be deleted. Please verify each object carefully before using the removal function.
If you are removing an application which is member of your list of login items, it will be removed from the list as well without reporting this in the table of deletion candidates. For technical reasons, this clean-up is limited to the current user, even if you had selected a search level including all users.
TinkerTool System contains several security features that prevent you from removing important parts of the system. You cannot remove components which are official part of macOS. You also cannot remove applications which are currently running on the local computer.
You should never use this function for software components which have not been installed by a drag-and-drop operation. Applications that came with their own installers or have been using the macOS Installer, usually had a technical reason to do so. In this case it is very likely that more than the usual components have been installed in the system, so they are not following the rules for self-contained applications. The Uninstallation Assistant cannot work as designed in that case. You should remove such applications following the instructions of their vendors.
Special Launch of Applications
You can use TinkerTool System to launch applications with non-standard options that are not the default when using Finder, Dock, or Launchpad. The following special settings are available:
- The system should not ensure that windows of the application are brought to the foreground and its main window gets the input focus. This means it does not become the active program that listens to keyboard and mouse. Instead, TinkerTool System stays active.
- macOS should not add the program to the application section of the Recent Items menu.
- Even if the application is running already, a new copy should be started.
- The application should hide after launch, so it should not open with any visible windows.
- All other applications should hide. The launched application should become the only visible one.
The last two options can be enabled at the same time. However, macOS will automatically try to resolve this conflict, making sure that at least one application stays visible. The detail behavior may depend on the operating system version you are using.

- Open the sub-item Special Launch on the pane Applications.
- Drag the icon of the program you like to launch from the Finder into the field Application to launch. You can also click the button […] to navigate to the application, or click on the white area to enter the UNIX path of the object.
- Set the options you would like to use.
- Click the button Launch.
Privacy
In addition to user permissions, macOS supports other features to protect the privacy of users and to secure data. One of those mechanisms is based on privacy settings that prevent access to certain domains of a user’s personal data in relation to applications. For example, access to the personal calendars of users can be configured in such a way that only the Calendar application of macOS has permission to process the calendar entries, but no other Apps, even if those Apps have been started by the user owning the calendar.
The decisions which applications should have access to which areas are stored by macOS in a privacy database. All entries can be reviewed in the table at System Settings > Privacy & Security. TinkerTool System offers a user interface to perform Apple’s official procedure to reset these permission entries. The decisions that have been made in the past regarding access to personal domains can be undone, returning to factory defaults. This causes the affected Apps to lose their access permissions and to ask the user again for a decision, the next time access to personal data is attempted.
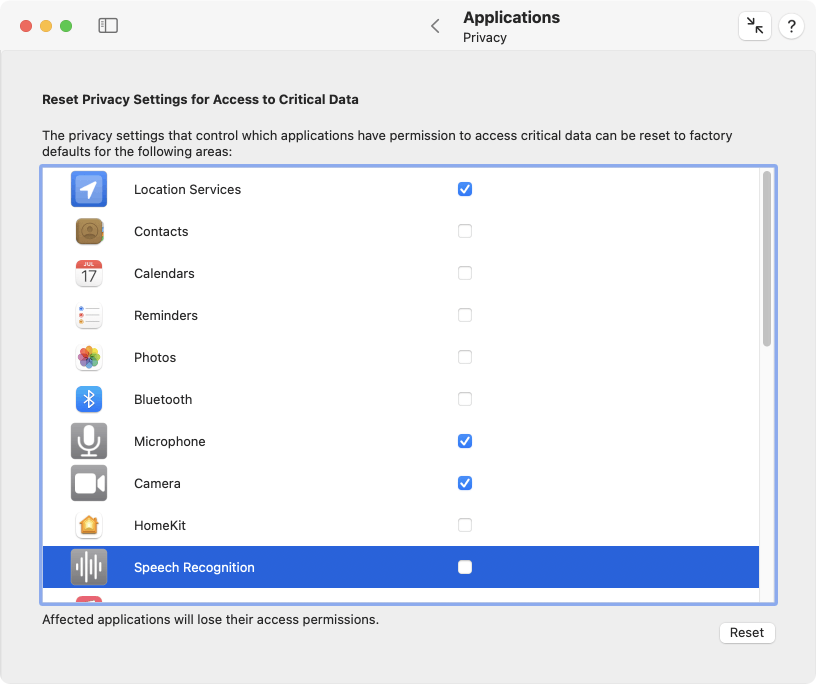
- Open the sub-item Privacy on the pane Applications.
- Set check marks for all access domains where the privacy settings should be reset.
- Click the button Reset.
Note that these settings are system-wide and take effect for all user accounts.
The number of items shown can be very different depending on your operating system version.
Security Check
To be protected against malicious software, macOS uses several different security techniques that complement each other:
- the quarantine feature that detects Internet downloads and tracks all files which are part of the download or have been indirectly created by the download,
- the code-signing technology which allows to recognize if a software component has been created by a known, trusted source, and which also detects possible subsequent modifications of files or memory pages by the use of digital seals,
- the notarization by Apple which certifies that the application had been submitted to Apple for review prior to its release to check for known viruses or similar malware,
- the application sandbox which ensures that a protected program cannot get access to specific system functions unless both Apple and the original software developer have explicitly granted such access. Each permitted type of access is called an entitlement. Programs protected in such a way come with an attached list of entitlements, digitally sealed in the application bundle. macOS launches such a program only after putting it into a sandbox first, enforcing compliance with Apple’s restrictions of the sandbox and the specified entitlements. The entitlements are basically exceptions that give the application running in the sandbox a certain right it doesn’t have by default.
- the hardened runtime environment which is basically an additional “light version” of the sandbox that applications can use to block themselves from using one or multiple of the following features of the operating system:
- use of the just-in-time compiler for JavaScript code
- generating code in memory at runtime
- changing behavior of the dynamic code linker via environment variables
- dynamically linking to code libraries of third parties
- modifying code in memory at runtime
- attaching to other applications in the role of a debugging tool
- access to microphones or similar audio input
- access to the built-in camera
- access to Location Services
- access to the user’s Contacts database
- access to the user’s Calendar data
- access to the user’s Photos library
- posting Apple events to other applications
- the Gatekeeper component, technically known as security assessment policy subsystem of macOS, which combines all functions and verification steps of the aforementioned features to eventually determine whether a given program should be considered “safe enough to execute,” or not.
TinkerTool System can evaluate a given software component, such as an application, a code bundle, e.g. a plug-in, an executable file, or a signed software distribution disk image, against all mentioned security checks, showing all details. This allows you to verify the integrity, the source, and the overall security assessment of this software.
Checking a software product is very simple. Just perform the following steps:
- Select the sub-item Security Check of the pane Applications.
- Drag the icon of a software object from the Finder into the field Object to check. This can either be the bundle of a standard macOS application, a single executable file, or a signed software distribution disk image (DMG). You can also click the button […] to navigate to the object, or click on the white area to enter the UNIX path of the object.
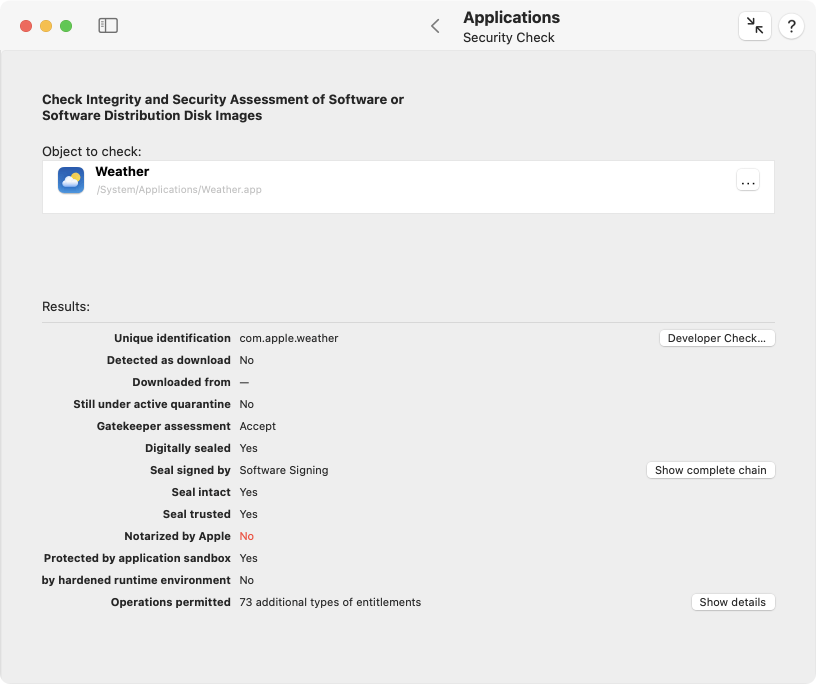
TinkerTool System and the security features of macOS will now analyze the selected software. This may take a few seconds, depending on the size of the bundle and the number of embedded subcomponents. The results will be displayed in the lower half of the window:
- Unique identification: the internal unique name used by macOS to identify this application. (Single executable files may not have such an identifier.)
- Detected as download: A Yes value indicates that quarantine markers are set for this application, so it has been detected that the selected program comes from a download.
- Downloaded from: If the application has been confirmed to come from a download, this entry will indicate the download source. It is usually specified as Internet address (URL) of the server which delivered the product.
- Still under active quarantine: Here, a Yes value confirms that the quarantine is still active, so a user opening the application must first confirm to be aware that the files come from the potentially unsafe Internet.
- Gatekeeper assessment: This line shows the official evaluation of the Gatekeeper component of your system, after having checked all mentioned security aspects and the policy you have currently set at System Settings > Privacy & Security > Security > Allow apps downloaded from…. The result can either be Accept or Reject.
- Digitally sealed: The value Yes indicates that the software has been signed and protected by a digital seal.
- Seal signed by: This line shows the name of the entity that code-signed the application. After clicking the button Show complete chain, TinkerTool System will show the entire chain of trust that confirms the validity of the digital signature. Entries are listed bottom-up in order of authority. The topmost entry repeats the name of the party who signed the software. The subsequent entries confirm (in compliance with each party’s certification policies) that the signature of the preceding line is genuine. The entry at the end is usually a CA, a Certificate Authority which is the root of this chain of trust.
- Seal intact: The value Yes confirms that the selected application has not been modified (in a way which has not been explicitly permitted by the party signing the application) after it was signed.
- Seal trusted: This indicator reflects the most important aspect of the digital signature, namely whether the seal was signed by a party trusted by Apple. Because anybody who has the necessary technical knowledge could sign and seal an executable program, this is what makes the signature actually meaningful to assess whether it might be safe to run the program. The trust indicator also confirms that some additional checks have been passed successfully, e.g. that there are no contradicting signatures in an application which contains multiple code parts.
- Notarized by Apple: If the component is notarized, this will confirm that the software meets certain basic security requirements. Apple has additionally checked that this software was “virus-free” at the time it has been published.
- Protected by application sandbox: A Yes value confirms that the selected application is protected by the macOS Application Sandbox when the program is launched.
- … by hardened runtime environment: A Yes value indicates that the application is self-restricted by the macOS hardened runtime environment.
- Operations permitted: Three possible results can be listed here: The entry Full sandbox protection without exceptions indicates that the selected program cannot get access to any “unusual” right. Apple’s sandbox for applications will be in place with the highest possible security settings. The status Only restricted by user permissions is the opposite, indicating that no sandbox will be used at all. An entry of the pattern xx additional types of entitlements confirms that the program will be sandbox-protected, but it will need some exceptions from the default rules, specified by a list of additional rights the application must have in order to work correctly. xx is replaced by the actual number of entitlement types needed. To see the complete list, click the button Show details. The table in the detail sheet describes each entitlement and, if applicable, shows a variable aspect of the entitlement in the column Object. For example, if an application should be granted permission to read the contents of the known folders A and B in the user’s home folder without informing the user first, there will be two entitlements of type Read access to specified file in home folder without confirmation, one referring to the object ~/A and one referring to the object ~/B.
Many applications that are part of macOS are shown with the Gatekeeper assessment Reject. This is not an error, but the correct result. Most of Apple’s built-in applications indeed do not comply with Apple’s own security guidelines. However, this won’t matter because the affected programs have not been downloaded off the Internet and come from a source trusted by Apple.
All executable files which do not have the form of a macOS application bundle are always rejected by Gatekeeper. Examples are command-line utilities or plug-ins. This is the correct and intended behavior.
Code can be sealed anonymously, i.e. without specifying a valid signature. This is known as ad-hoc signing which will be indicated by a respective marker in the line Seal signed by….
A software distribution disk image can contain multiple applications. If you are testing such an image file, TinkerTool System will only show the security assessment for the container itself. Information exclusive to applications (like sandbox protection) will be missing. A sealed image file should guarantee that its checksummed contents is authentic as well. However, to see the actual results for the individual applications, you’ll have to open the image and point TinkerTool System to one of the files inside.
Only modern disk images can be signed. This security feature is mainly used for software products targeting macOS 10.12 Sierra or later.
Apple has defined a high number of entitlements which are not documented, so they are not known to the general public. Only Apple, and in some cases a few selected developers who could not solve problems with the sandbox otherwise when using the known standard set of entitlements in their applications, have permission to use these undocumented “holes” in the sandbox. TinkerTool System lists these entitlements with the notice Unofficial entitlement and the internal name Apple uses for the related right.
Additional Checks for Software Developers (macOS Sonoma or later only)
If you are using macOS 14 or later, macOS and TinkerTool System will offer two additional checks that are of interest to independent software developers. Different security and “packaging” rules apply to applications developed not for the Apple App Store, but for independent distribution. Developers can test whether an application’s current security settings, signatures, and packaging are designed so that the application
- can be submitted to Apple’s notarization service, or
- that it can be started on any end customer’s computer, i.e. not just on the publisher’s development Macs.
If the test fails, Apple will refuse to accept the application or Gatekeeper will prevent it from starting, respectively.
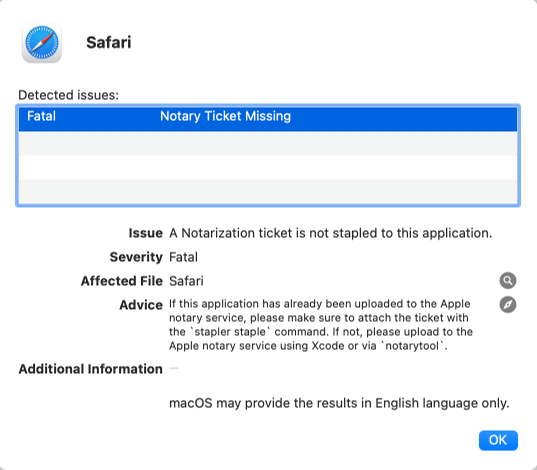
If your system and the currently selected application meet the requirements, you can run the tests as follows:
- Press the Developer Check… button that appears at the upper right of the results list.
- In the dialog window, select which of the two tests you would like run.
- Click Run or press the return key.
After waiting a while, the results will be displayed in another dialog window. All detected errors, problems, and notes are listed in a table. Details are shown in the lower area of the window after clicking on a line in the table. If a specific file in the application bundle is affected, you can reveal it in the Finder by clicking on the magnifying glass icon. If Apple provides manuals or similar documentation with more detailed information about this issue, you can access them on the Internet using your standard web browser by clicking the compass icon.