The Pane Operational Safety
Application Integrity
On the pane Applications you may have used the feature Security Check already, which is designed to examine different aspects of an application under security considerations.
The pane Operational Safety allows you to run a specific part of this check, namely the one based on protecting executable code by digital seals (codesigning), for a large number of applications at the same time, e.g. for the entire system volume. This makes it possible to quickly assess the overall security situation of a computer.
The check considers the following items:
- Is each application digitally sealed and does each seal meet the security requirements of the currently running operating system?
- Has any application been changed after it was sealed?
- Is each seal trustworthy?
The bulk check is limited to applications for the graphical user interface. As part of such a test run, you cannot check code for the command line, or other sealed components, like disk images, for example.
- Select the tab item Application Integrity of the pane Operational Safety.
- Drag the folder with the applications you like to check from the Finder into the field Top folder to check. You can also click the button […] to navigate to the folder, or click on the white area to enter the UNIX path of the folder.
- Click the button Check.
It is possible to choose not only a folder, but an entire volume for the check. The bulk check is automatically limited to one volume even if it contains links to other volumes.
The check can take a long time, depending on how many applications are contained, and how large they are. Particularly large applications, like Xcode or complex computer games, for example, can greatly lengthen the test. During the test run, the button Stop on the wait panel can be clicked to cancel the check.
For technical reasons, test runs that have been started already may not be interrupted immediately when clicking the Stop button. TinkerTool System may continue running some of the test jobs in the background (which still can put load on your Mac) but will then discard the results. To cancel all running checks immediately, you must quit the application after clicking the Stop button.
After all test procedures have been completed, the final results will be shown in a table. It lists all applications with their names and marks the aforementioned aspects of the check in the last three columns, using icons:
- Sealed: the application is digitally sealed using Apple’s codesigning technology.
- Intact: the seal is not broken, i.e. all components of the application are still unchanged, and nothing has been added or removed. The requirements of the running operating system in respect to the seal are met.
- Trusted: the seal was signed by a party currently trusted by Apple.
The following icons are used:
- green dot: the test was passed
- red cross: the test was not passed
- empty field: the test could not be performed
After selecting a line in the results table, details about the application and its check will be shown. The button with the magnifying glass can be used to reveal the respective application in the Finder. If there was a failure, the line Detected issue indicates the reason why the test was not passed.
You can also click the button Close and run full security check on selected application in order to open the program on the pane Applications, letting it perform a complete security test.
By clicking the button Text Report you can create a copy of the result table in text form. This report can either be printed or you can export it in Rich Text Format to a text file.
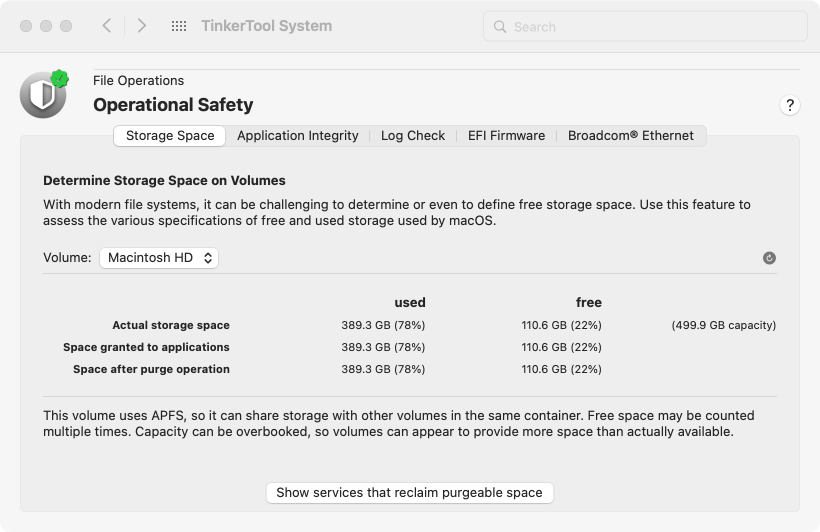
Storage Space
With the latest versions of macOS, users are regularly confused as to how much storage space on a given volume is actually free and allocated. This confusion has several causes:
Applications may use different definitions of memory units when referring to storage space without correctly labeling it. 1 kilo byte may represent 1,024 bytes or 1,000 bytes, depending on definition. Apple has changed the guidelines for presenting storage space multiple times in the last years. Detailed information on this topic can be found in chapter Basic Operations, section Display of Memory Sizes.
Applications may show storage space from a user’s point-of-view (Finder) or from a technical point-of-view (Disk Utility). For example, the Finder considers storage space allocated for local Time Machine snapshots to be free. This should signal to the user that the storage space used for that purpose could be freed automatically by the operating system when it is needed for something else. Some applications explicitly differentiate between “free” and “available” space, where “available” is defined to be “free plus purgeable”. For further information, please see the chapter The pane Time Machine.
Modern file systems can use special management technologies for the administration of storage where capacity may be counted several times although it exists only once in reality.
Apple’s APFS is one of these modern file systems. Among others, it supports the following technologies used today, which can lead to confusion regarding storage space specifications:
APFS no longer needs partitioning. Within an APFS zone on a disk drive, multiple volumes can be created without the need to divide them into partitions. (A zone administered by APFS is however a partition itself, the APFS container, in order to separate it from the areas not maintained by APFS.) Volumes in the same container can share their storage space, i.e. free blocks don’t need to be permanently assigned to a single volume, but are potentially available to each of the volumes. Consider an APFS container with 250 GB, containing 4 volumes: We have 4 volumes of 250 GB, so apparently 1,000 GB of space, although 250 GB are available in reality only. To capacity is overbooked, which would only become an issue when each of the volumes actually tries to allocate its registered maximum storage.
APFS supports a snapshot feature. If desired, a file system can “remember” its state at any given time across the entire volume. At the touch of a button, this condition can be restored within seconds. Any number of these “frozen” states can be created as long as there is still free capacity to store the old and current version of all data. Technically, the snapshot feature works by no longer discarding deleted or overwritten data blocks, but keeping their former contents. Note that the storage space used for this does not become visible at the file level. The volume will need more storage space than the sum of all currently stored files, however. Modern backup systems typically use snapshots.
So if a volume is using APFS, the question for free space may not be easy to answer.

TinkerTool System can show the different views on storage space supported by macOS for each volume:
- Select the tab item Storage Space of the pane Operational Safety.
- Choose the desired volume with the pop-up button Volume.
The system volume is internally split into a read-only system part, a read/write part for data, and an update snapshot volume. However, this is usually hidden by macOS, and all three volumes share the same storage space, so they are presented as single volume in the pop-up button.
The different definitions of used and free storage space will be presented in a table also listing total physical capacity. When APFS is in use, a corresponding warning will be shown below the table. When comparing the results with other applications, please remember to set the correct unit for measuring memory in TinkerTool System as intended. See Basic Operations, section Display of Memory Sizes.
- Actual storage space: the physical space allocated on the volume for use.
- Space granted to applications: the space available to applications without any restrictions. For safety reasons, a certain reserve is taken into account for the operating system itself.
- Space after purge operation: the storage which will become available when the operating system is forced to delete “unimportant” data automatically to regain more actual space. This difference between the true free space and the potentially free space is called purgeable storage by Apple. The actual meaning of this can vary depending on the system version. For example, this could be media files of rental movies already played, which could be downloaded again from the cloud at any time, or it could be local APFS snapshots created by Time Machine.
What Apple actually means by a purge operation to reclaim storage space is not exactly defined.
However, you can press the button Show services that reclaim purgeable space to show the list of all system services that have currently registered with macOS to free storage space when necessary.
Check the system log for suspicious user activity
To ensure the security of a Mac that is open to the public, it can be helpful to automatically scan the system log for entries related to user authentication or the authorization of privileged operations. If there is an accumulation of an unusually large number of failures (e.g. entering incorrect passwords), it can be assumed that intrusion attempts have taken place. Publicly accessible can hereby mean that the keyboard and screen (called console in classical data processing) are not in a monitored location, e.g. in a school workroom. However, it can also mean that protected services that require a user to log in can be accessed from the local network or from the Internet.
TinkerTool System can evaluate the existing system log regarding the following operations:
- successful and failed logins at the macOS login screen,
- successful and failed logins on the lock screen, i.e. after exiting the screen saver or after waking from sleep mode,
- all unsuccessful attempts to authorize a privileged operation, both locally and when accessed through a network service.
This list does not claim to be complete. It is not possible to predict how long entries will remain in the system log. This depends on the respective operating system version, individual settings, use of maintenance functions and available disk space. FileVault logins occur outside of macOS and are therefore typically not included in the log.
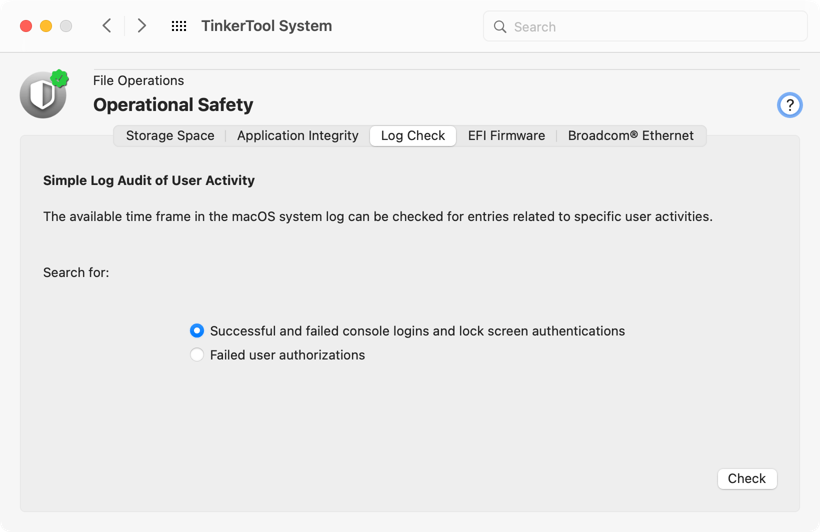
To start the evaluation, select the desired item under Search for and then click the Check button. The search may take some time depending on available log size. The results will be shown on a separate sheet window.
- When evaluating the console and lock screen data, successful logins are highlighted in green, failed ones in red.
- When evaluating the authorization of privileged operations, all listed entries refer to failures.
The overviews are computed based on original excerpts from the system log. Therefore, they usually contain quotes which depend on the respective macOS version.
EFI Firmware
On Macs with Apple Silicon, this feature is not available, but also not necessary. Such Macs are specially protected against firmware modifications.
To start a computer and to load an operating system, an additional program, a kind of mini operating system, is needed that takes over this task. This program must be built into the computer and is therefore called firmware. This software is not so firmly anchored in the hardware however, otherwise it could not be updated and adapted to technical advancements itself. For this reason, it it stored in a special, electrically erasable memory, similar to flash memory. Apple updates the firmware in regular intervals without special notice, as subordinate task when updates of the “normal” operating system are installed as well.
The firmware is protected against manipulation by multiple measures. Nevertheless, with some criminal energy, it is possible to inject malicious programs even in the firmware, e.g. spy functions. This kind of attack on a computer is difficult to detect, because under normal circumstances the firmware is considered built-in and immutable.
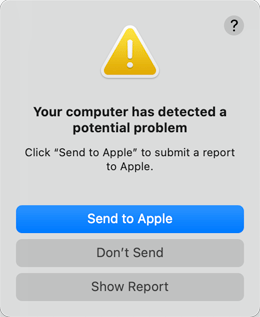
For security reasons, Apple checks in regular intervals in their latest operating systems whether the firmware is still intact and unchanged. Block checksums of all firmware versions ever distributed for a respective Macintosh model are provided via Internet for this purpose, comparing it with checksums of the current firmware found. Such integrity checks are run in the background and only become noticeable if an anomaly has been found. An example warning is shown below.
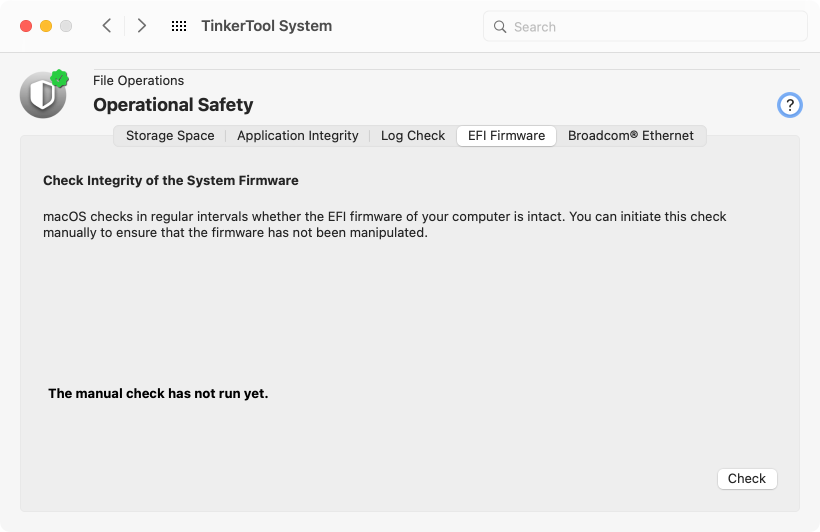
TinkerTool System can initiate such a check manually, so it is possible to test and verify the integrity of the system firmware immediately. Perform the following steps:
- Select the tab item EFI Firmware of the pane Operational Safety.
- Click the button Check.
The test result will be shown in a user dialog and additionally in the window itself.
Not all Macintosh model series support this type of firmware check. TinkerTool System will notify you in such a case. Especially the latest model series are affected where the computer is monitored and protected by an independent processor running its own operating system (Apple BridgeOS), or where the Mac uses an Apple processor (Apple Silicon). On such a Mac, macOS cannot read the firmware any longer, and certainly cannot write it, so security is guaranteed by other means.
It can happen that Apple publishes a new version of macOS that installs a new firmware, but does not contain an up-to-date checksum for this firmware. In this particular case, the integrity check will fail. However, such a failure usually triggers an internal update of the checksum list via Internet, if the setting System Preferences > Software Update > Advanced > Install system data files and security updates is enabled, which is the default. So if you see an integrity warning shortly after a macOS update, repeat the integrity check after a few hours to verify whether this may have been a false alarm.
It can be normal to receive a false alarm if you are testing unreleased beta operating systems.
Broadcom® Ethernet
On Macs with Apple Silicon, this feature is not available, but also not necessary. Such Macs are specially protected against firmware modifications.
Ethernet ports made by the vendor Broadcom are characterized by the special feature that their firmware is also updatable in a relatively simple way. Monitoring this firmware is therefore security-critical as well.
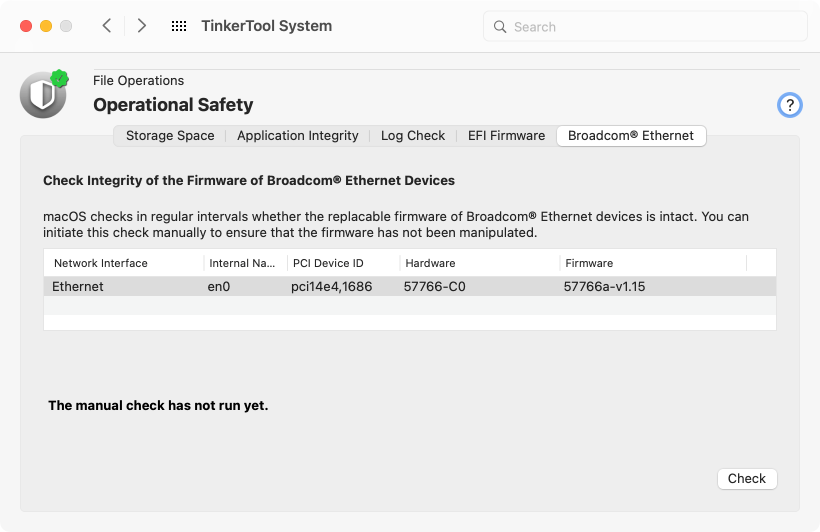
TinkerTool System can check if one or more Ethernet ports made by Broadcom are built into your Mac, or attached externally. If yes, their firmware can also be tested for possible manipulations:
- Select the tab item Broadcom® Ethernet of the pane Operational Safety.
- Review the table whether affected Ethernet devices are present in your system. If yes, click the button Check.
The results of the check will be shown after a few seconds. If multiple ports are present, a number for each tested item in the report, the PCI device ID, is associated with each unit. You will find this number as back part in the column PCI Device ID in the table, allowing you to find the corresponding network interface.
macOS only checks Ethernet devices of the vendor Broadcom. Ethernet ports of other vendors are not tested, but usually have no vulnerable firmware either.